

Hi-Tech Security Solutions held its first invitation-only Executive Breakfast Seminar in July at Fairlawns in Johannesburg. The event was sponsored by Ideco and ADI.
The topic was the role of biometrics in the future of business, with speakers from Ideco, Risk Consultancy Network and ADI. Starting off, Clem Sunter presented the morning’s keynote. Sunter is a great speaker, he engages the audience from the word go and offers revealing insights into the potential future of the world and South Africa.

The accuracy in the science, or art of assigning probabilities to scenarios is something people differ on, but we need something to be able to make a judgement call when assessing probably outcomes. So while Sunter presented his scenarios as well as the probabilities of them occurring, he stressed that scenario probabilities are not an exact science, yet.
An additional caveat is that scenarios change, sometimes rapidly and the probabilities presented in July might be different as you read this.
On the global front Sunter offered a few future global scenarios with two holding the best probability of happening. The first of these Sunter called Hard Times, in which the world is looking at five to 10 years of low growth, in other words, a flat economy. This is bad news for everyone, but he noted that if you can offer value for money and innovation in this environment, your business can still thrive. Sunter says the Hard Times scenario has been assigned a probability of 40%.
The second option he called Ultra-Violet, or UV. In this world we will see a distinct difference between the old economies and the new. Old economies will grow slowly – the U-curve in economic performance. The new economies will grow at three-times the rate of the old and change the structure and power players of the world we have become used to. This scenario is a bonus for the emerging markets, assuming governance and drive to support entrepreneurs is present from governments. The possibility of Ultra-Violet happening is very dependent on whether China keeps growing and is assessed at a 30% probability.
Among other probabilities, the chance of a double-dip recession was set at 20%.
Local is nervous
On the South African front, Sunter offered three scenarios. The first sees the country remain in the top 59 nations of the world. The threat to this scenario is that policy uncertainty deters foreign investment, which would see the second scenario happen, in which South Africa joins the bulk of Third World countries, poor but peaceful, as foreign investment flees and tax revenue declines. In this reality, BRICS is likely to become BRINC, where Nigeria outplays South Africa and makes new friends.
If you add violence to the above, the third scenario of unpredictability and violence becomes a reality, something we do not want. Sadly this scenario’s probability has risen from 0% a year ago to 10%. The first scenario has fallen from a 70% to a 50% probability. The second scenario is ranked at 40%.
Among the issues that will make or break South Africa is that of land distribution in which land invasions and the confiscation of farms without recompense is a major factor, along with issues such as nationalisation and violence.
After a brief question and answer session, Sunter’s book on the fox trilogy quickly sold out. More information on Sunter, scenario planning, his take on future scenarios and his books is available at http://www.mindofafox.com.
Integrated identity management
The biometric-focused presentations followed breakfast. Below is a brief overview of some of the information delivered by the presenters. Marius Coetzee from Ideco kicked things off with a presentation on integrated identity management.

Coetzee highlighted the core problem in many of today’s fraud scenarios as that of identity. People can easily commit a crime by ‘borrowing’ a card, password or PIN (CPP), or even duplicating cards with ease – as many consumers have found to their dismay. Using systems like these that allow for fraud to be committed with ease results in losses running into billions globally.
The problem with CPP is that while the credentials offered are correct and mostly authorised to conduct transactions, there is an identity gap between validating the credentials and the actual identity of the individual using them. If you enter a password, you are simply verifying that you have entered the correct password, not the identity of the person who is supposed to be associated with that password.
Biometric technology overcomes this because the identity of the person is inextricably linked to the biometric. For example, using fingerprint biometrics will ensure that only the appropriate person gains access to the relevant places, data or applications. Coetzee admits that even as little as five years ago it was possible to fool a biometrics system, but the leaders on the field have advanced technology to the extent that are far more reliable than CPP solutions today.
The drive to biometrics is being led by governments around the world. In India, for example, the government has embarked on a process to biometrically identify all its 1 billion citizens.
Of the many biometric technologies available, fingerprint technology has gained over 60% of the market, with facial and iris recognition taking second and third spot. In South African courts, the only biometrics accepted are fingerprints, facial and signature.
Figure 1 shows the various biometric technologies available and their place on the technology maturity curve.
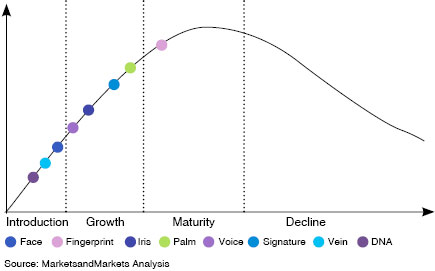
Coetzee went on to explain how fingerprint biometrics readers work and what part of the individual’s fingerprints make these prints unique. He also touched on the importance of proving your selected biometric technology effectively, as many products cannot live up to their promises.
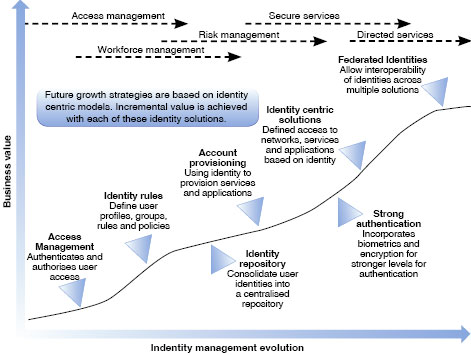
Furthermore, Coetzee stressed that biometrics is not simply another security technology to add to your list. When correctly planned and implemented, it integrates with far more than time and attendance software and can deliver measurable business value. See Figure 2 (The evolution of identity control).
Coetzee also introduced Ideco’s GreenBox, which hogged the attention of attendees in the exhibition environment after the event. The GreenBox in a nutshell offers:
* Multifunction input device.
* Integrated FICA/RICA station.
* Enables paperless transaction.
* Document process automation.
* Fast system integration.
* Small desktop footprint.
* No storage of paper records.
* USB Powered.
Where to with biometrics
The next speaker was Dave Casey form Risk Consultancy Network. As a consultant, Casey looks at what was happening in the biometrics market from different angles. To start, he mentioned a few of the normal objections to using biometrics. These included:
* Security is a grudge purchase – biometrics is expensive.
* Acceptance of the technology has been slow based on ignorance, concerns about privacy and secure data storage.
* Biometrics is slow – cards are quicker.
* Cannot justify the cost verses the benefits.
* Biometrics can be compromised.
* Resistance from unions.
* Biometrics is not 100% accurate.
* Has not worked in the past.

While all these issues are valid, Casey adds that they have all been dealt with to certain extents over the past few years. Of course, if you opt for the cheapest piece of technology available, you are sure to run into trouble, but that applies to whether you are buying a biometric reader, a car or basically any product.
Discussing biometrics being used for authentication, Casey says it is the preferred option for accurate and reliable data and application access, especially in the financial industry. When used in conjunction with other measures it offers optimal security for high-risk facilities and dramatically reduces the risk of identity theft.
However, he warns that companies looking at biometrics cannot simply buy what sounds like a good deal. “Do not believe the specs written on the box,” he advises. Do your own proof of concept as it pertains to your environment. The technologies are evolving and improving all the time, what did not work in 2005 will almost certainly succeed now.
Casey also touched on the reason for the slow uptake of biometric solutions in business. Basically, the blame can be placed in the hands of everyone. For one, consultants that fail to advise clients on the right solutions because they do not have a solid understanding of the technology and its capabilities in the real world and fail to balance the key variables of accuracy, quality, reliability, speed of performance and cost.
Secondly, installers also get the blame because they are driven by a profit motive and push the wrong technology just to make a sale. Clients who do not take the time to educate themselves are also asking for problems as they can easily be swayed by these installers and consultants.
Vendors also get the blame because they claim their systems can deliver specific performance, not mentioning that the performance was tested in a lab in perfect conditions. When you add real-world conditions, imperfect lighting and dirty workers to the mix, the products fail. Again, Casey strongly advises companies to run their own proof of concept exercises in their specific environments.
Then there are social factors against biometrics as well as innumerable YouTube videos showing how badly biometrics perform – not mentioning that the technology in these videos is five or even 10 years old.
As a consultant, Casey is not beholden to biometrics companies and notes that Frost and Sullivan expects the biometrics market to grow from $4,5 billion in 2010 to $14,7 billion in 2019. “Biometrics is fantastic technology and is here to stay. It is improving every day and will form part of more and more applications as time goes by.”
And for those on the forefront of technology, Casey says the latest biometric to come out of the labs is based on the human tongue. It will be interesting to see what readers they develop for tongue prints.
Biometric trends within system integration
The final speaker was Gordon Moore from ADI Global Distribution. He looked at the impact of biometrics today and where it would be going in future, before delving into real-world case studies showing the value added by integrating biometrics into business applications.

Biometrics is gaining traction in our daily lives (if somewhat slower than in business and government) in numerous ways. We can see the technology appearing in the form of biometric locks for homes, biometric safes and even in luxury cars. Moreover, medical aids are looking at using biometrics to curb the massive fraud they face, as are hospitals focused on improved patient care and preventing the theft of babies. Some smartcards have biometric details embedded in them, as the new South African identity card will have, should it ever see the light of day.
An important new entrant into the identity market is near-field communications (NFC) which will allow people to use their smartphones as a means to identify themselves and transact. Of course, people will need to verify that the cellphones they are using are theirs and they have the authority to conduct transactions. This will initially be handled via PINs, but we have already seen some phones with biometric fingerprint and even facial recognition attached.
In the business world, and specifically in the industrial and mining sectors, the focus on the Hi-Tech Security Solutions Executive Breakfast, biometrics is growing rapidly in areas such as access control and time and attendance. However, Moore says we are also starting to see it in areas such as visitor management, employee verification and outsourced labour management.
Furthermore, Moore says that in the health and safety field, biometrics is proving its worth in areas such as restricting access to specific areas that require specific skills, such as heavy machinery and vehicle operations. Using biometrics ensures that only people with the correct training can access and use certain equipment.
An example Moore presented of integrating biometrics into current business processes in the logistics environment grabbed people’s attention. In this simplified version of the case study, biometrics was used for:
* The validation of orders,
* Use of a forklift via a biometric starter,
* Picking the stock via a biometric-enabled wireless hand held scanner,
* The validation of delivery/receipt, and
* The generation of an audit trail of the process, which can be linked to a time-synchronised video trail using security cameras.
Moore also gave an example of the savings a company would attain by using biometrics merely as a time and attendance technology. A spreadsheet of the example can be seen in Figure 3.
Moore then offered a brief introduction to the use of biometrics in the convergence of physical and logical security operations. He demonstrated how integrating biometrics into your current processes will not only improve security, but also reduce the administration of what are currently independent silos of identity control within an organisation. In terms of finances, this integration will also prevent fraud as people will not be able to claim that someone used their passwords or stole their cards, or in this case, stole their fingerprints.
The day ended with a demonstration of a few biometric technologies, including Ideco’s GreenBox, which kept many attendees occupied long after the event’s close.
Hi-Tech Security Solutions would like to thank all our speakers and those people who made the time to attend.
| Tel: | +27 11 543 5800 |
| Email: | malckey@technews.co.za |
| www: | www.technews.co.za |
| Articles: | More information and articles about Technews Publishing |

© Technews Publishing (Pty) Ltd. | All Rights Reserved.