
IP video management systems (IP VMS) used in video security today have an increasing need to deliver new services and features to a large and ever-growing class of new users. These users’ roles go beyond the traditional security mission.
Providing these new services and features becomes even more complicated across multiple independent systems. Some IP VMS solutions rely on system federation to connect multiple systems. However, a different approach – aggregation – offers improved ease of administration and better overall system performance.
Previously thought of as mainly security focused, the camera and data feeds monitored by a traditional video management system (VMS) are now being used to manage day-to-day operations, ensure policies are being followed, and ultimately make organisations run more efficiently. Recognising video system data more broadly as information that can inform all kinds of decisions has led to growth in the base of VMS users. Growing businesses are hungry to consolidate and put this information to good use, driving optimisations across their organisations.
An expanded mission for IP video systems
In the broad sense, business owners, security administrators and their responsible delegates are looking to maintain some level oversight across their organisation. More and more, this oversight is extending beyond the traditional security considerations and into operational ones.
The regional manager of a retail store wants to ensure a promotion is set up correctly without driving to each store.
A facilities representative at home wants to validate that an off-hours alarm is a credible threat before dispatching local law enforcement, avoiding potential fees for nuisance alarm responses.
A factory manager utilises security camera feeds to ensure conveyor belts are running as expected, potentially even detecting belt failures prior to breakages, minimising risk to employees and improving factory up time.
An airport uses analytics built into security cameras to calculate the wait time at security check-in locations and updates signs directing passengers to shorter lines, thus improving customer satisfaction.
These newfound uses for what was previously video security specific data require more effective ways to manage and distribute access.
The problem
New user types are being added to the traditional VMS user base, beyond the standard security officer, supervisor or operator. Demands are being made from marketing, operations, facilities and more to leverage the information captured by the security deployment.
Additionally, an increased expectation of connectivity, driven largely by expanding networks and the proliferation of mobile technology, is placing new demands on systems that previously could have been close-looped. Users need access to pertinent information, often from multiple systems available whenever and wherever they happen to be.
Administrators need to ensure that the right people have access to the right information at the right time across these global distributions. An influx of non-security and untrained operators is placing new demands on user interfaces, driving the need for customisation and simplification to ensure that the data a given user needs is what is made available to them.
Traditional video management systems were optimised around the security and surveillance user – supporting CCTV-style keyboards and calling up cameras by camera number or selecting a camera from a lengthy list of cameras, sophisticated search queries for finding and retrieving recorded video, and even more complicated export processes to ensure the authenticity of evidence.
While these systems continue to evolve to further incorporate the needs of security operators, the resulting interfaces and architectures are becoming unbearable for non-security operators.
Finding and displaying a megapixel camera on a monitor in the security operations room is one problem. Serving up a view of that camera and all other related cameras from twenty different stores for the regional produce manager of a grocery chain working on a laptop from his hotel room is quite a different problem indeed.
In order to best meet these diverse needs, Pelco by Schneider Electric is pursuing an approach using proven, standards-based technologies which provide the necessary structure to manage geographically and logically distributed systems.
By treating the VMS as an information system and grouping disparate VMS system information together, employing an aggregated architecture similar to those used by news aggregators and Web-hosting companies, critical information can be both centrally managed and accessed by the user base.
An aggregation solution
Pelco’s aggregated architecture approach decentralises the actual information, by keeping it local, while centralising its flow, or the access to it. This has several advantages over current available models focusing on system federation, where information within a federation must be synchronised across the systems.
Among these are reductions in overall system complexity, reductions in cross-traffic due to synchronisations, less concern over link failures creating database synchronisation problems, more efficient latency management and improved load balancing opportunities. The introduction of the aggregation layer also provides an effective way to provide access to new enhancements for a legacy install base.
These benefits stem from a reduction in data duplication and database synchronisation operations across the system. Traditional VMS systems have had the ability to connect to multiple, independent systems for several years. The DigitalSentry system from Pelco by Schneider Electric, for example, uses the ControlPoint client to connect to any number of systems and display the cameras and recorders from those systems.
However, if a given user’s permissions change to where that user needs to now see a new camera or be prevented from seeing an existing camera, it is important to have a method of updating clients and servers with new credential information.
Active Directory and LDAP interfaces help, but still require a considerable amount of synchronisation information to be exchanged between different servers. This same problem is also present in traditional federated solutions, which attempt to coordinate access across systems by sharing, synchronising and replicating database information.
An aggregation approach, on the other hand, treats each system as an independent entity, pulling from the relevant systems at run time, through the client interface. While permissions exist on each independent system, through the aggregation interface, an administrator can manage permissions and push changes out from a central location; pertinent information can be captured into one database and shared with other enterprise applications instead of repeating the same function on each independent system, one at a time.
While the aggregation architecture enables centralised access to and management of the broader organisation, it accomplishes this by providing and facilitating access to the relevant local systems rather than storing a representation of the full organisation of systems and attempting to keep that synchronised. This allows the structure to be separated from the user access/permissions management, pushing those decisions downstream; thus allowing it to scale more appropriately.
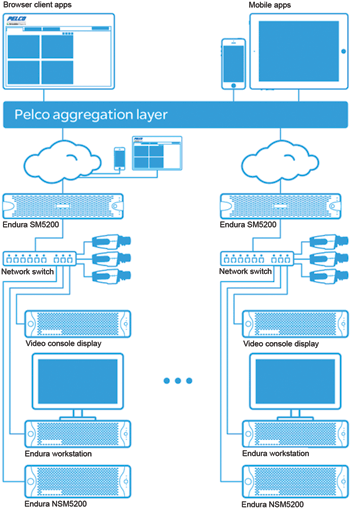
As depicted in the diagram, each site can be effectively managed locally as an independent entity. When an organisation determines that it is necessary to see across all their installations, the aggregation server software can be installed, creating the aggregation layer.
Once installed, the aggregation layer is accessed via the same user experience interface being distributed with Pelco products today. There is no waiting period while the local databases synchronise with some central authority or with each other. The only difference the user sees is that they now log into the aggregation server.
System aggregation in a nutshell
System aggregation cleanly allows a system administrator to group information across distributed systems by leveraging proven information sharing architectures and disciplines. Pairing the topology with Web-based user interfaces further simplifies the sharing of information to users regardless of where they are or what device they are using.
For more information contact Pelco by Schneider Electric, +27 (0)11 254 6400, johann.schoeman@schneider-electric.com, www.schneider-electric.com

© Technews Publishing (Pty) Ltd. | All Rights Reserved.