
Shortly after the announcement that BriefCam is to be acquired by Canon, Asaf Bar, BriefCam’s sales director for the Middle East, Africa and India, paid Hi-Tech Security Solutions a visit with the company’s South African master distributor, ISDS. The reason for the visit was to introduce the next generation of BriefCam’s video content analytics platform.
BriefCam has taken its unique fusion of Video Synopsis and Deep Learning to the next level with BriefCam v5. These capabilities redefine how video surveillance systems are being used by law enforcement agencies and major enterprises globally. The uses of this technology are many, including streamlining and reducing time spent reviewing video by pinpointing people and objects of interest, for safety and security, and also identifying trends in behaviour for extracting quantifiable insights.
The BriefCam video content analytics platform has three integrated modules: Review, Research and Respond.
Review and search
As demonstrated by Bar, this version collates information from multiple video streams at the same time, the maximum number dependent on your processing power. By first selecting your timeframe, the system detects, extracts and classifies all objects on the streams you select from your VMS and superimposes the objects on the stationary background, simultaneously displaying events that have occurred at different times, with the ability to link back to original video. The user is then able to refine the categories of their search, by a lengthy list of classes. For example, only showing women, men, children, cars, trucks, animals, etc. The synopsis quickly filters out everything not requested and allows for further refinement.
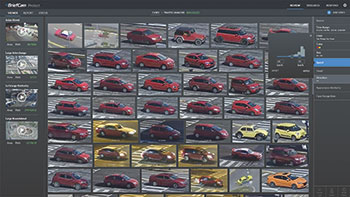
The user can specify a female wearing red and carrying a bag, for example, and the system identifies all objects from the video streams meeting those requirements. If you are looking for someone running away from a crime scene, you can also exclude all people not moving faster than a certain speed in a particular direction.
The same applies to vehicles. You can get a synopsis of all vehicles travelling at over 30 kmph in your parking area over the course of a day, for example. You can also get a synopsis for everyone walking or driving along a specific path (which you define with your mouse) over the period of time the user is interested in.
The new version of BriefCam also has facial recognition and attribute similarity. There is currently no functionality to identify people via facial biometrics, but it is possible to build a synopsis of all the faces seen on your video streams over the selected timeframe. Once again you can filter the results and select a person to see where they have been, across all cameras.
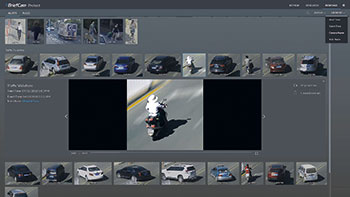
Bar notes that the next version of the application will have improved facial recognition allowing for use of external source, and the ability for users to create blacklists and whitelists of people allowed in the environment.
Planning and research
The second module is a business intelligence tool that allows users to uncover quantitative insights within their video data and provide reporting and analytics to enable data driven decision making for various areas of the business. Users can build any report they choose – such as footfall in a retail environment for each hour of the day – and these will be available at the click of a button. They can also be automatically generated and sent to specific people on a regular basis.
Bar says customers will be able to create almost limitless intelligence with the feature, including tracking people and vehicle movement patterns over time, determining demographic trends associated with time, identify crime hotspots and even tracking employees’ adherence to safety regulations automatically.
The reports are designed through a point and click process, which means they can be generated quickly while delivering valuable and actionable information.
Proactive response
The third module is the real-time option that monitors live camera feeds and can trigger alerts on certain defined conditions. For example, cars making an illegal U-turn at a specific intersection or travelling the wrong way down a one-way street can be immediately brought to the attention of the relevant people, or people walking in an exit-only access point can be highlighted and tracked.
The options are, again, almost limitless and triggers can be set for people and vehicles loitering, entering restricted areas, or even parking for too long in drop-off areas. All while the surveillance system is still used for its normal functions by the security staff.
For more information on what Briefcam can do, please see the video examples at https://www.briefcam.com/resources/videos/.
| Tel: | +27 11 543 5800 |
| Email: | malckey@technews.co.za |
| www: | www.technews.co.za |
| Articles: | More information and articles about Technews Publishing |

© Technews Publishing (Pty) Ltd. | All Rights Reserved.