
South Africa dominates the annual listings of the best African universities. The prestige of its higher education institutions has made them sought after by students from many countries, and in some cases foreign students make up between 10 and 30% of all students. Security is an essential matter in maintaining this level of attractiveness.
Most students who last year participated in the ‘Fees Must Fall’ protests did so peacefully, but images of a violent minority were seen around the world. As everyone involved in this field knows, just a few problematic incidents are enough to tarnish the image of a peaceful and secure environment that is the result of years of effort and implementation of good security practices.
Universities face specific security challenges. Their campuses comprise many diverse areas, such as education buildings, residence halls and outdoor spaces, that need different security procedures.
There are diverse physical and psychological threats, including thefts, muggings, vandalism, assaults and other examples of violence against students and staff members. Preventing and countering such different dangers also requires different security procedures to be established.
In February’s edition of this magazine, several campus protection managers highlighted communication as an essential part of responding to incidents: communication between key players like university directors, security staff, law enforcement authorities and protesting students.
There is currently a need for security management software solutions that can speed up communication between these key players by promptly supplying the proper procedures to be followed for each type of incident. Agora SMS (Security Management Software) is an example of such a software solution.
Procedures, procedures, procedures…
As soon as an incident has been identified, Agora shows the security operator the proper procedure to be followed, such as, for example, calling on law enforcement or simply closing a gate. This reduces response times, whether the incident is a burglary, a fire or simply a broken window.
The procedures implemented with Agora also provide for night escort patrols, which are increasingly requested at universities all over South Africa. Agora provides this service, which is so important for post-graduate students and members of staff leaving the university at late hours when there is almost nobody around.
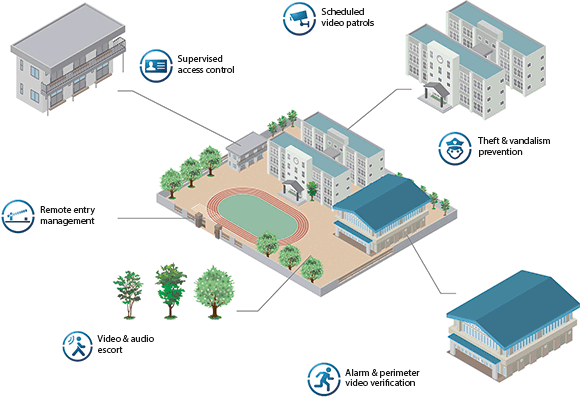
Agora also allows configuring procedures for daily on-demand situations, such as delivering keys or requesting cleaning and maintenance services. Agora displays to the security operator the proper procedures to streamline the resolution of routine situations that, although common in everyday campus life, could potentially represent a security threat or a future liability.
In short, Agora provides pre-defined and auditable procedures, thus enabling a more effective, quicker and less costly security management when compared to the option of increasing the number of guards patrolling the campus on foot.
Centralising information and management based on real data
Agora does not live by procedures alone: it also stands out by automatically selecting the most suitable camera for evaluating a certain event, however far away it is taking place. If control centres receive better information, it is possible to drastically reduce the number of false alarms, a situation that causes operational disturbances as well as unnecessary costs.
With ubiquitous control from a central point there is no need for multiple control centres spread around the campus. All the data collected by cameras and sensors is channelled into the same place, which is also, of course, good news for university budgets. Also, sensible security data is safely stored at a unique restricted-access location.
The data collected by the software also makes it possible to improve operations by using its business intelligence tools. Agora provides university security officers with activity and incident reports that are essential to allow them to achieve the best balance between tight security supervision and resource allocation.
There are many reasons for Agora to be used in South African universities. Investment and resources are used to their best, running costs are reduced to an optimal level, and most importantly, the identity that makes South African universities so attractive to students is preserved.
For more information contact Bernardo Motta at [email protected]

© Technews Publishing (Pty) Ltd. | All Rights Reserved.