

A centrally managed video surveillance platform has been unveiled by Keystone Electronic Solutions, a South African electronics research and development company. Dubbed ‘Project V’, the system differentiates itself from others in that it is built around the central concept of event triggering, whereby it performs video streaming upon specific events/alarms, in addition to providing a video-on-demand interface.
At a launch event at the Pretoria Country Club on 13 October, John Eigelaar, Keystone director and co-founder, introduced the local security industry to the features and benefits of the solution. “We are extremely excited about Project V. As far as we are aware, there are no other products available today that can match this technology. We have had a dedicated team work on this project over the past few months and have had a few field trials with select customers. Project V can overcome a number of challenges for our customers – it makes security and surveillance much easier and more effective, and thus creates a huge cost saving,” he commented.
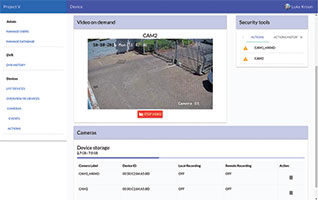
The solution comprises remote site equipment in the form of Keystone’s Remote Site Monitoring (RSM) unit, and a surveillance platform deployed in a central data centre. All user access to the central platform is provided through a web interface which is accessible via a standard web browser without the need to install or maintain any user applications.
The ‘stream on trigger’ video platform is not only able to provide digital video recording (DVR) archiving on the central Project V server, but also at remote sites. Integration with customer systems, such as network management systems, access management systems, trouble ticket management and reporting tools, can be provided through an open application programming interface (API).
Certain video triggers can be set up to either start or stop the video recording and streaming, while real-time streaming makes it possible for security teams to determine how to respond to a security incident. For example, in the event of intruder detection alarm, security teams will be alerted and will be able to see live video, allowing them to more effectively judge how to respond to the situation.
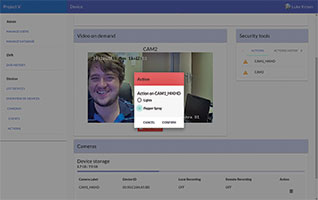
Project V integrates with any IP camera, and any I/O interface that a camera might provide (such as zone or movement triggers) can be integrated as part of the site security profile. The RSM unit is permanently connected to the cameras and will pull available audio visual (AV) streams from the cameras depending on the alarm/event triggered. Streams can be stored locally or pushed to the central server for remote recording or live viewing.
To make allowance for differing data bandwidth access across a full range of applications and site infrastructures, bandwidth can be selected on each onsite unit. Depending on this setting, the AV video will either be streamed to the Project V server or recorded locally on the unit. In both cases the alarm events will be transmitted across the CnE (command and event pipe) over the network. Operators can also request AV streams/recording from the web graphical user interface. The platform allows for the backhaul of the CnE pipe and the AV streams, either across an Ethernet WAN interface or the onboard 3G GSM modem.
Project V was designed to be highly scalable from an interface point of view, and the number of I/Os available to the system is easily scaled from a standalone device to a large installation by adding further RSM I/O modules.
For more information contact Keystone Electronic Solutions, +27 (0)12 460 4135, john@kses.net, www.kses.net.
| Tel: | +27 12 460 4135 |
| Email: | ivan@kses.net |
| www: | www.kses.net |
| Articles: | More information and articles about Keystone Electronic Solutions |

© Technews Publishing (Pty) Ltd. | All Rights Reserved.