
The introduction of what is commonly referred to as a ‘black box’ marked an important milestone in aviation history. The black box or to use the more precise term flight data recorder (FDR), is used to preserve a flight’s recent history by collecting multiple parameters several times per second. The FDR, combined with the cockpit voice recorder (CVR), which captures the audio including pilot conversations, provide an accurate testimony of a flight’s history, and assists in any further investigation.

A painful lesson that has been learned during investigations of aviation accidents and incidents. In order to accurately compose the sequence of events that led to an incident, it is critical to capture all flight data parameters together with the pilots’ conversations. In other words to gain insight from past events it is critical to examine the data parameters of various systems as well as human conduct.
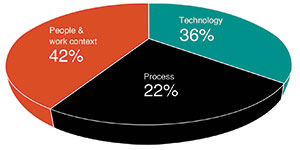
This theme is very much aligned with the findings of the Abnormal Situation Management (ASM) consortium that argues that there are three principal types of sources or causes of abnormal situations:
• People and work context factors.
• Equipment and technology factors.
• Process factors.

How is that relevant to incident management solutions?
Continuous improvement enabled through process excellence and a culture of high performance are key attributes for organisations wishing to maintain a leadership position in today’s markets. To this end, incident management solutions should provide tools that analyse an incident’s complete data, as shown in Figure 2.
Mining an organisation’s incident performance data allows organisations to detect inefficiencies in processes and/or SOP (standard operating procedures). It can also identify sub-par performance of both individuals and teams relative to an organisation’s benchmarks, and discover anomalies in system performance as reported by IoT (Internet of Things) sensors.
Conducting an analysis with methodologies that have been proven to provide continuous improvement, such as Six Sigma, is critical for organisations that want to create and maintain an adaptive culture.
Black boxes have played an invaluable role in improving aviation safety by dramatically reducing the volume and magnitude of incidents and accidents. Today’s incident management solutions should capture all incident data to provide organisations visibility into how incidents have unfolded. In addition, with the right analytical tools, they should allow them to extract valuable insights that can transform the way these organisations work. In the same way that that black box has transformed the aviation industry.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.