
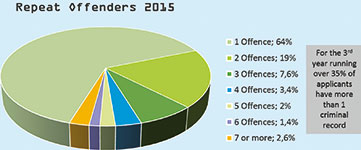
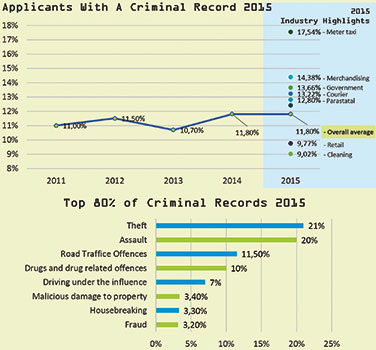
In the retail industry, companies rely on their point-of-sale (POS) personnel to act as their representatives, provide excellent service and protect the interests of the company by preventing in-store theft. Unfortunately, companies also open themselves up to loss in revenue from these very same employees through various POS frauds and theft.
This is common in all sectors of the retail industry and companies have tried to budget for the loss in revenue by adding a percentage to product prices. The problem with this is that companies are losing competitive edge by increasing product prices and employees that do commit POS fraud, or theft, feel free to commit the crime over and over until they are eventually caught red-handed.
Catching employees in the act has spawned an entire new range of technology solutions, such as NUUO’s POS Solution. The NUUO POS Solution combines surveillance video with transaction data from POS and ATM. All scanned items can be displayed on live view, playback and used to trigger user-defined alarms. For example, NUUO POS solution sends an alarm to alert the manager when a transaction is voided. The system will store all the transactions and special events in a secured, keyword-searchable database with video attached for easy review.
NUUO’s POS Solution allows the manager to instantly playback a transaction or search for a specific video months after a transaction. This helps to reduce the hidden shrink from employee theft, sweet-hearting and other POS frauds.
POS fraud
There are two main methods of committing point of sale fraud (Information source: brisbaneacfe.org):
• When a sale is targeted (a real customer is involved):
Void sales: Void sales fraud generally target cash sales. The employee will sell an item to a customer, hand the item to the customer and take the money from the customer, but will either not ring up a sale or ring up a void sale.
Sales processing: No matter what system is used, a dishonest employee may process a sale to an accomplice but recording the sale price for a cheaper item than actually taken by the accomplice. Of course, this fraud may be done without the sales person knowingly involved. They may just not notice that the price tag does not match the item – and this will be their defence even if they are involved.
Sweet-hearting: This is when employees give away merchandise without charge to a ‘sweetheart’ (family member or friend) by making as though they scan the product but don’t. Different sweet-hearting techniques include covering the barcode, stacking items and only scanning the bottom one, and bagging the item without even scanning it.
• When a false return is made (fictitious customer is used):
False returns: The aim of a false return fraud is to process a fake return of goods and to steal the money allegedly paid back to the (fake) customer.
For more information contact MIRO Distribution, 086 123 MIRO, riandi@miro.co.za, www.miro.co.za

© Technews Publishing (Pty) Ltd. | All Rights Reserved.