
Milestone Systems’ open platform IP video management software (VMS) is integrated with Bosch Access Control and has been certified with full documentation of testing results and best practice for optimal configurations. This means that Bosch and Milestone customers can count on a reliable, interoperable solution, and installing partners can take advantage of the practical information in the certification documents for better implementations.
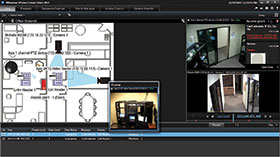
The integration between the Bosch Access Control system and the Milestone XProtect VMS was achieved earlier with the user interface via the Bosch system, and subsequently upgraded with the XProtect Access Control Module in 2014, with the certification process completed by the end of the year. The combined solution now displays real-time access control events and alarms in the Milestone XProtect Smart Client, also providing control of doors, gates and barriers from within the video interface. Live video and views of recordings are synchronised with all the access control events.
The XProtect Access Control Module is part of the Milestone Integration Platform Software Development Kit (MIP SDK). The XProtect Smart Client provides a unified interface to the Bosch Access Control system with such dedicated functions as monitoring access events with video verification, manually assisting passage (controlling doors, gates, etc.), conducting investigations of specific access points or cardholders, easily exporting video evidence and generating reports.
Video of the Bosch access incidents visually confirms and informs on situations as they happen for verified decision-making and efficient response. The video also provides easily shareable evidential documentation for analysis, rectification or prosecution.
The seamless integration of Bosch Access Control with the XProtect Smart Client means Milestone customers can keep their easy-to-use video interface while adding access control – without having to re-train. The integration delivers real-time monitoring with video verification for fast response to incidents, including locking, unlocking or triggering a system lockdown. Users may also choose to work with the Bosch interface, and the access control main system administration remains within the Bosch system.
For more information contact Milestone Systems, +27 (0)76 811 7495, mme@milestonesys.com, www.milestonesys.com
| Tel: | +27 10 500 8793 |
| Email: | gep@milestonesys.com |
| www: | www.milestonesys.com |
| Articles: | More information and articles about Milestone Systems |

© Technews Publishing (Pty) Ltd. | All Rights Reserved.