
Today’s volatile economic climate demands that each corporate investment be supported by a strong business case. Justifying security management solutions is no exception, especially when executives expect security professionals to prove return on security investment (ROSI).
Older methods for calculating ROSI were complex and relied on soft data to derive numbers. A more tangible way to justify security investments is to organise ROSI into three levels: security effectiveness, risk reduction, and business efficiency.
1. Security effectiveness: Protecting people and assets
The first level of security effectiveness represents the basic reason why executives invest in security management solutions: to protect people and assets. Common and visible systems are used, such as security cameras and access control devices.
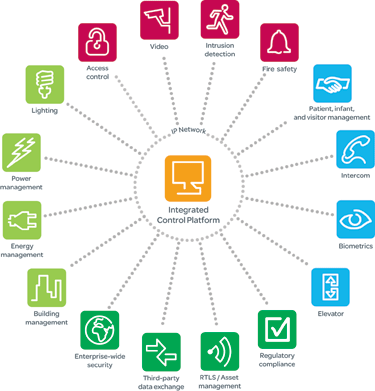
Organisations can realise lower capital expenditure (CapEx) costs and lower operating expenses (OpEx) by integrating these disparate technologies onto a single IT network.
Proving the value of security effectiveness alone is problematic because businesses cannot determine with certainty whether incidents simply did not occur, or whether the security solution prevented the potential incidents from taking place. At a basic level, security effectiveness ensures a secure business environment.
2. Risk reduction: Enhancing business continuity
The second level is risk reduction, which aligns with the goals of executive management. Security leaders identify internal and external risks to the business by asking: “How will the organisation benefit financially by securing itself against these risks?” This type of solution provides better situational awareness, bolsters business continuity, and helps organisations avoid financial ramifications of unexpected incidents.
Schneider Electric helped a global leader in the medical research field reduce risk when new government regulations threatened to disrupt existing processes. Management inventoried the substances subject to the regulations and designed new security processes relevant to them, providing protection for the business and facilitating compliance. After 30 months, the team realised:
* 30% less time needed to respond to an event.
* 430% reduction in nuisance alarms.
* Reduced guard staff costs.
* Lower administrative costs for generating compliance reports.
Assigning monetary value to risk reduction is possible because most executives can readily quantify the hourly or daily cost of a business shutdown. They can also estimate the potential financial liability if an accident were to occur.
3. Business efficiency: Enhancing business performance
The most impactful ROSI level is business value that transcends security – when security becomes an essential contributor to business success, profitability, and continuity. This is achieved by determining how security technology can add value by making core business processes more efficient.
For example, Schneider Electric helped a major car manufacturer realise added business value at its manufacturing plant. Optical turnstiles were integrated with access control devices at each assembly line to count workers and ensure credentials at the beginning of the day. The production line would not operate if all qualified staff members were not present, reducing the risk of costly mistakes and quality compromises, and ensuring smooth operations.
In order to achieve maximum ROSI, the key is to make security an essential part of corporate culture. When people, process, and technology work together in an intentionally designed symmetry, organisations reap benefits that cross operational boundaries.
Schneider Electric has global security expertise and a proven portfolio of successful implementations that reflect all three levels of ROSI. Our security solutions can integrate many different security disciplines into a single system. The resulting single-seat view of the entire security domain delivers real-time, actionable information that enables better decision making and faster response to events. To drive even more value, the security infrastructure can easily and cost-effectively be integrated with other building systems such as, lighting, energy management, building management, power management, and IT management.
Source: Pelco Press Summer 2013. Used with permission.
For more information contact Pelco, +27 (0)12 254 6400, malcom.govender@schneider-electric.com, www.pelco.com

© Technews Publishing (Pty) Ltd. | All Rights Reserved.