
In the article (http://www.securitysa.com/15825r), we looked at the perimeter security options estates have available today, but the focus was more on non-surveillance options, although one respondent did mention thermal cameras as a good perimeter security measure when integrated with other technologies.
With modern analytics and the improved performance of cameras, it’s worth taking a second look at perimeter security, but focusing on the surveillance solutions available, for both visual and thermal cameras. And while we would not suggest departing from the tried-and-tested perimeter security solutions, it is fair to say that surveillance-related solutions can resolve many perimeter challenges when properly installed and integrated with the central security command centre.
With this in mind, Hi-Tech Security Solutions asked Heino Hacke from Axis Communications what he thought the ‘ideal scenario’ was for perimeter security from a surveillance company’s perspective.

“I have, through the years as a perimeter security specialist, seen many different technologies used for perimeter security, from cheap and nasty to expensive and sophisticated,” Hacke says. “I have seen products and solutions come and go, but at the end there is only one solution that always wins hands down and that is a top-tier thermal solution with detection analytics. When it comes to price, in most cases your top-tier solution works out less if you calculate the total cost of ownership (TCO) over the lifespan of the system, plus it will save you from the frustration of having faults and issues from a substandard solution and prevent a false sense of security.
“As my dad used to say: ‘You buy cheap, you buy twice’. You must first look at quality: quality of the product, quality of the after sales support, level of the system integrator proficiency and importantly, the false alarm rate. If you choose the right system from the start, it will save you from having to reinvest for rectifying an obsolete and problematic solution.”
For the same question, Luke Liu from Hikvision SA is of a similar opinion. He says it is crucial to keep residents and visitors safe with comprehensive, reliable perimeter security solutions. He points out that in the past, advances in technology and hardware have vastly improved perimeter security systems, but consistent, reliable verification between true and false alarms was still lacking.
“Conventional perimeter protection solutions provide certain detection features enabled by video content analysis, such as motion detection, line-crossing detection and intrusion detection, but would simply compound all event detections, triggering frequent alarms when an object is detected. This could be an animal, a shadow, or other natural movements. As a result, security personnel needed to spend time to investigate each one, potentially delaying any necessary response and generally affecting efficiency.”
Consequently, he advises that an ideal perimeter security solution must feature ‘effective false alarm reduction’ and ‘quick target search’ capabilities, which can identify and react to perimeter breaches in real-time and to automate footage searches to quickly locate true events.
“Let’s raise AcuSense technology as an example,” Liu says. “Hikvision’s AcuSense embeds deep-learning algorithms into security cameras and video recorders to differentiate people and vehicles from other moving objects, allowing security teams to focus on real threats. With high accuracy, the system disregards alarms triggered by other objects such as rain or leaves and delivers alarms that are associated with human or vehicle detection. It also has a ‘quick target search’ feature that allows security personnel or local police to find footage quickly in the event of a security incident. This saves many hours of searching for footage manually.”
Long perimeters and surveillance
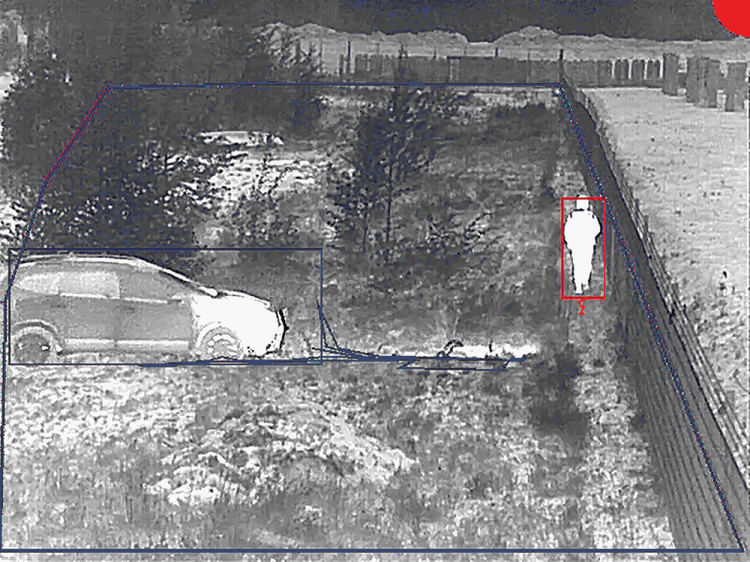
Having cameras on the perimeter is by no means a new idea, but is it a good idea when your perimeter is kilometres long? In addition, detecting a breach is one thing, but what about where the intruders go after the breach as it can take some time for a guarding team to arrive on scene. A PTZ can track someone, but only if manually controlled from the command centre or if effective analytics are in the camera.
Hacke says thermal cameras with optical PTZ for tracking are an absolute necessity in most cases, even if the analytic on the PTZ can track the perpetrator for a limited time. The core of a successful perimeter solution must adhere to the basic five perimeter security principles: detect, verify, identify, track and deter.

“It is all about verification, verification if there is an actual breach and/or a false alarm. False alarms and alarm fatigue are a major issue when it comes to perimeter security, you need to know that if there is an alarm, there is a potential breach. If there is a breach you need to know where and what it is. Only top-tier thermal cameras with proper analytics can offer you such a low false alarm rate. When it comes to distance, thermal cameras can cover hundreds of metres with a single camera. This also means that you are using less equipment, have less points of failure and less maintenance, once again lowering your TCO.”
He boasts that when it comes to best detection and lowest false alarm rate, Axis Perimeter Defender (APD - Edge Analytic) is one of the leaders in the market. “We celebrated the launch of our new thermal model that has AI at the end of last year. The AI analysis verification on APD is built on top of the proven 3D analytics to further verify between false positives and positive alarms, differentiating between animals and actual humans and vehicle detection, lowering the false alarm rate even further.”

Liu points out that sometimes “two technologies are better than one” and security solutions that integrate video and radar capabilities are a good example of this.
“By bringing video and radar together, we can achieve ‘multi-dimensional awareness’ in perimeter protection. The first awareness ‘dimension’ comes from radar, which allows an estate to detect people or vehicles crossing the perimeter boundary and to follow them around to ensure they only access authorised areas of the site. The second ‘dimension’ is smart, high-resolution video, which helps security personnel identify potential security threats quickly, see exactly what occurs and respond faster to security breaches to protect people and assets. “
Hikvision has created an all-in-one radar PTZ solution. This combines a Hikvision radar sensor with a latest-generation Hikvision PTZ camera with deep learning capabilities to help identify security threats and respond faster to incidents. When the Hikvision radar sensor detects a moving object, an alert is sent to the integrated PTZ camera, which zooms in and focuses on it to see if it is a human or vehicle. An alert is also sent to the security team automatically if it is not a false alarm, helping them respond faster to reduce potential intrusion risks.
No brand is an island
As mentioned above, surveillance technology is not the only solution one needs for a secure perimeter. Whatever surveillance options an estate opts for, it needs to be able to integrate into other systems and platforms, or have other systems integrate with it to allow, for example, for a PTZ to be triggered to focus on a breach.
Liu explains that Hikvision is dedicated to encouraging and supporting third-party integration with its products. “We are continually expanding our third-party collaboration by offering a range of integrated solutions, providing multiple options for customers and delivering integrated service to our partners and customers. We fully support open standard protocols, but also created a dedicated team to focus on building the integration protocol and related development tools.
“With Hikvision SDKs (software development kits), we provide comprehensive programming sources to help customers develop their own solutions. Additionally, we have released the ISAPI, an open standard protocol that provides even more possibilities for customers.”
Similarly, Hacke says: “At Axis Communications, one of our three core values is ‘Always Open’. This is not just for our company culture and about transparency, but this even filters through to how we design and develop our products. Even before IoT got its name, Axis Communications was one of the first electronic manufacturers that adopted an open platform model whereby anyone can integrate with our product. We also follow standard integration protocols that make it easy for third-party applications to communicate with our devices.”
Specific perimeter offerings
Looking more closely at what the companies offer estates in terms of perimeter solutions, Liu notes, “Hikvision offers diversified solutions for residential estates and gated communities, which boast highly-effective false alarm reduction for them to achieve efficient and secure perimeter protection. Solutions range from deep learning algorithm-based video products (AcuSense) to thermal cameras (Heat Pro) and radar products (the all-in-one radar PTZ solution).
Hacke advises potential buyers to look beyond just the price of the products. “Do not make the mistake of just looking at product and price when you choose a solution. You need expertise and the support so that you invest in a solution that works and will work for many years.
“Axis offers a five-year warranty on all our products as well as five-year firmware and RMA support after the discontinuation of the product. We offer system design tools to our system integrators to successfully design and implement the solution, with that we also give them the training as well as the ACP (Axis Certified Professional) international certification to make sure they are fully trained as specialists in their field.
“Pre-sales support from Axis Communications includes proof-of-concept, system design and solution advice. Other software we offer at no cost is Axis Device Manager and Axis Device Manger Extend, with this software your tech support can do health monitoring remotely on your system and be proactive on any abnormalities before there is a system or device issue, keeping your devices online.”
| Tel: | +27 11 548 6780 |
| Email: | [email protected] |
| www: | www.axis.com |
| Articles: | More information and articles about Axis Communications SA |
| Tel: | +27 10 085 8300 |
| Email: | [email protected] |
| www: | www.hikvision.com/africa/ |
| Articles: | More information and articles about Hikvision South Africa |
| Tel: | +27 11 543 5800 |
| Email: | [email protected] |
| www: | www.technews.co.za |
| Articles: | More information and articles about Technews Publishing |

© Technews Publishing (Pty) Ltd. | All Rights Reserved.