
When considering people to keep the control room running effectively and deliver the service to clients, it is also important to make sure your operators have been through an effective vetting process to mitigate the human risk, which include fraud and collusion.
The question of what kind of attributes operators in a control room require was addressed in Craig Donald’s article earlier in this issue.
Vetting, or screening, can ensure the people you hire don’t have criminal records and that they are who they say they are. Hi-Tech Security Solutions asked Jennifer Barkhuizen, head of communications at Managed Integrity Evaluation (MIE), and Jenny Reid, director of iFacts, for some information around background screening and vetting of potential new hires.
Our two interviewees work for independent companies that provide vetting services to clients. We asked them if it was necessary to use a third party. Surely a company’s HR department would be able to follow the same processes to do background checks and the like?
“Onboarding a new employee into an organisation can be a time-consuming process, especially if the correct procedures are followed and the correct background screening checks are conducted,” says Barkhuizen. “Using an external service provider will give added assurances and peace of mind that all background checks are conducted in a legitimate and compliant manner.”
Reid agrees, noting, “Many companies believe that they can do their own background checks or screening on companies or individuals. While this is perfectly true, is it cost effective? Companies may not have direct access to the various bodies whose information needs to be verified, such as CIPC, SARS, Department of Labour, etc.”
When it comes to what specifically needs to be examined, this will naturally differ depending on the industry and the job description. Barkhuizen explains that a reputable service provider would be able to advise a company on what solutions and services would work best for the position they wish to fill.
Start with the basics
“For any position, whether entry level or management, the most important checks to conduct will be qualification and criminal verifications,” she adds. “Psychometric assessments add a lot of value in determining the likelihood of the individual to be successful in an objective manner. Companies have the option to either use short screening questionnaires or very comprehensive psychometric assessments. These are available across all levels within an organisation.
“It is also important to vet a candidate’s previous employment by doing reference checks, as this will provide additional insights as to how a candidate operated at previous employers.”
This does not apply on a one-off basis, however, and Barkhuizen says it is important for companies to create a background screening policy to be adopted as part of their company HR practices. “The policy should be applied for appointments at all levels, company-wide to avoid any negligent hiring choices.”
According to MIE’s statistics, the following verifications are the most requested for onboarding new staff at all levels: Qualification verification, criminal record checks, credit checks, ID verification and employment reference checks.
Additionally, Reid says that If you are outsourcing the control room service, it would generally be to a security firm of sorts and it is therefore essential that the vendor verification process includes industry-specific checks, including PSIRA registration, provident fund details, CIPC information, SARS clearance certificate and a letter of good standing from the Department of Labour regarding the Workman’s Compensation Fund.
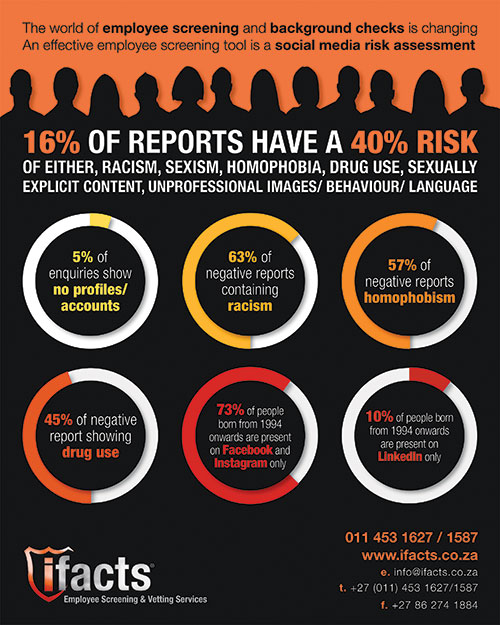
“If the company is suitable it would then be recommended that all the staff are screened for PSIRA registration, criminal record check, verification of ID and personal contact details (including previous employers), reference checks and an integrity assessment. Management staff should also be assessed for leadership skills and a social media risk assessment should be conducted.”
Reid also notes that to conduct screening tests, the company must ensure that it has the necessary consent forms in place and that procedures adhere to all legislation.
The social media risk
In a world that is seemingly dominated by social media, many individuals and companies have been caught making inappropriate comments on social media. Some of the more publicised situations and the implications are well known to all. It would therefore be a wise move for companies to also check up on potential employees’ social media profiles to avoid any later unpleasantness.
Barkhuizen adds that social media profiles present a wealth of information on users and the analysis of this can also be used to identify any potential red flags around a candidate’s suitability to the business culture. It can also be leveraged to gain a deeper understanding of an employee’s career aspirations. Such data can be mapped back to job roles or growth and development trajectories for improved employee satisfaction, which is known to have a significant impact on productivity.
“Many online platforms most frequently used by consumers have surpassed being a mere tool and have become a lifeline to information about the world around them,” she adds. “While businesses have been using social media optimisation for several years to aid in marketing themselves to the public and learning more about their consumers, it is now also being used more progressively as a tool in their recruitment efforts and to assess and vet potential employee candidates.”
The world of background screening and employee vetting has come a long way and today there are many different options for companies looking to hire new employees. The cost of doing a thorough job can often cause concern for companies, but the cost of hiring the wrong person could be even worse. And then, as noted, the cost of having to deal with fallout from someone else’s social media mistakes, mishaps and stupidity could be the most costly penalty to pay.
So, while a full assessment from a third party may not be viable or even desirable in every instance, when looking at employees who are to be tasked with important decisions in a security control room, ensuring there are no potential problems is essential. In this instance, psychometric assessments may also be useful given the scope of their function.
For more information contact:
• iFacts, +27 11 453 1587, info@ifacts.co.za, www.ifacts.co.za
• Managed Integrity Evaluation (MIE), +27 12 644 4000, jenniferb@mie.co.za, www.mie.co.za
| Tel: | +27 11 543 5800 |
| Email: | malckey@technews.co.za |
| www: | www.technews.co.za |
| Articles: | More information and articles about Technews Publishing |
| Tel: | +27 11 453 1587 |
| Email: | admin@ifacts.co.za |
| www: | www.ifacts.co.za |
| Articles: | More information and articles about iFacts |

© Technews Publishing (Pty) Ltd. | All Rights Reserved.