

Given the increase in the use of fingerprint technology in public and private organisations, as well as some recent announcements on the reliability or lack or reliability of certain types of sensors and algorithms in the fingerprint biometric market, Hi-Tech Security Solutions spoke to some of the leading fingerprint biometric vendors in the market to find out more about the state of this market.
To cover the scope of what fingerprint biometrics offer, we started by asking how fingerprint biometric readers work and what and how they store the data they collect, how reliable they are and then moved into the usage thereof. And finally, we asked our interviewees how end users should make the decision as to what fingerprint biometrics they should look at purchasing for their particular needs.
Often when looking for input on an article like this, one has to dig around to get the information one can use. In this case, we received such a large amount of information we had to cut out a significant amount of data. Our information providers have put the effort in to take readers on a learning experience of what goes into fingerprint biometrics and what are the issues you, the buyer and user need to look out for when considering fingerprint biometrics for access and identity management. Hi-Tech Security Solutions appreciates their time and effort in supplying the below information. Our interviewees are:
• Deon van Rensburg for ViRDI,
• Walter Rautenbach for Suprema,
• Claude Langley for HID Global, and
• Gary Jones for IDEMIA.

ViRDI Distribution SA, Deon van Rensburg
ViRDI is a biometric brand from UnionCommunity Co. in South Korea. The company is active in over 120 countries, including in South Africa and the rest of Africa, and offers a range of biometrics devices, from fingerprint to facial recognition. Deon van Rensburg represents the ViRDI office in South Africa and up into Africa.
Although fingerprint biometric scanners use imaging technology (in the form of CCD or CMOS) to capture images of the fingerprint, most biometric vendors do not keep images of the fingerprint in the database.
Here I must add that it depends on what the application is. Level 1 and Level 2 scanners are for commercial use, i.e. access control and time and attendance and have no need for images to be kept in the database. Level 3 scanners are for governmental, law enforcement and banking use for identity management purposes and do keep images in the database. Level 3 systems also compare these fingerprint images to central databases such as HANIS or AFIS.
The process for extracting, matching and authentication is complex.
• The user presents their finger to the platen on the optical scanner of the biometric terminal.
• The optical scanner then extracts a number of images of the fingerprint in digital format.
• The extraction portion of the algorithm then extracts unique identifiable features from the digital image. We call these unique features minutiae points.
• Once these minutiae points have been identified and extracted, the system discards the physical images and everything is converted into a complex hexadecimal string that is unique to every vendor.
• This hexadecimal string is called a template.
• The template is then compared via the matching portion of the algorithm to the template that resides within the database.
• Dependent on the results, the user is then either verified, identified or rejected.
• The ViRDI system is unique in that it extracts two templates per fingerprint and then compares to two templates of the same fingerprint in the database. This provides us with faster and more secure transaction times.
International standards for fingerprint biometrics
There are two international standards available for commercial systems. ANSI / NIST-ITL-1-2011 (updated 2013 & 2015 and includes ANSI 378 & ANSI 381) and ISO / IEC 19794 (includes parts 4 & 8:2006). These standards indicate minimum requirements for greyscale, dpi, platen size, output format etc., as well as interoperability between different fingerprint biometric systems. According to the NIST website these standards “…supports the proliferation of low-cost commercial fingerprint sensors with limited coverage, dynamic range, or resolution”.
However, they are minimum standards and most Tier-1 vendors use proprietary algorithms that far exceed these minimum standards as well as proprietary scanning systems (what we call the fingerprint scanning module) that includes LED lighting technology, platen construction, lenses and optical devices.
The PIV/AFIS systems used by governments, law enforcement and banking have the MINEX standard since they compare, verify or identify fingerprints from a centralised database such as HANIS or AFIS and all images must comply to one set of standards since a fingerprint taken with a Level 3 PIV/AFIS scanner in South Africa must be exactly the same as one taken in the USA or Europe.
Safety, security and privacy
Reputable biometric vendors have been cognisant of the possibility of reverse engineering fingerprints and templates for at least a decade and they spend huge amounts of money on R&D specifically to prevent any form of fraud or reverse engineering. Governing the usage and storage of biometric data are subject to various standards and even legislation. ISO 27001, for instance, provides minimum standards on storage and encryption of such data.
Speaking from the ViRDI point of view on how we prevent reverse engineering: when our algorithm extracts the minutiae points from the fingerprint, we only include the data relating specifically to those minutiae points in the algorithmic hexadecimal string (or template). We then encrypt the template with a proprietary encryption that exceeds ISO 27001, very similar to a standard 512-bit encryption.
When data flows between terminal and database, the data is also encrypted using this proprietary encryption. If a ‘hacker’ was able to hack this encryption and was able to unearth the base hexadecimal string (template) and was able to reverse engineer the extraction algorithm, all he or she would find was the location of a few minutiae points on a fingerprint since we do not extract any other details, such as ridge flows (i.e. loops, whorls, arches, tented arches), ridge patterns or any such data required to reconstruct a fingerprint. Think of it as GPS coordinates with no map.
Specific scanning technology
ViRDI uses patented LFD scanning technology. This is a multi-step process. First, the platen is manufactured from Sapphire Crystal to make it scratch resistant for longer life span, and also to reduce the risk of transfer of bacteria. The scanning process is subject to a live fingerprint being placed on the platen. Until a live finger is placed on the platen, the complete fingerprint scanning module remains in low power state.
Once the scanning process activates, the fingerprint module bombards the fingerprint with multi-coloured LED light. By using this light source, we are able to achieve Multispectral Response Imaging, i.e. we do not solely use the epidermis of the fingerprint and the scanning process is subject to a number of factors inside the dermis that needs to be within acceptable parameters. Only once these have been complied with does the system begin taking images of the fingerprint.
This is also not a straightforward process as the lenses inside the fingerprint module have been specifically designed – and patented – by ViRDI for the best possible image to reach the image sensor. Once the images have been captured, the algorithm extracts two separate templates of the minutiae points and converts it into a template which is then encrypted using our proprietary encryption. Matching can either take place on the terminal or on the server, or at both locations.
The ViRDI algorithm is currently the highest rated commercially available for embedded devices with an EER (Equal Error Rate, which is a combination of FAR and FRR) of 0.234%, FRR of 0.1% and FAR of 0.0001%. Our algorithm complies with (and exceeds) ANSI / NIST and ISO as well as some more obscure standards such as WQL.
The question of whether it is worth paying more for our device than some cheap-and-nasty device is similar to the question asking why buy a luxury BMW as opposed to a TATA. Both have bodies, both have seating, both have wheels, both have engines, both have transmissions and both have the same basic function – transporting people from one point to another. So why buy one over the other? It comes down to reliability, safety, security, durability, speed of use and the extra features required to provide the solution the user requires.

Recommended technology
I would advise that South Africa pays more attention to LFD technology since fingerprint fraud from users is one of the biggest issues affecting us now, especially in the time and attendance vertical. If the system can also perform Multispectral Response Imaging it would be an added bonus. There is probably only a handful of Tier 1 manufacturers available in SA (and when I say available, I don’t only mean available for sale, but also having technical support, repairs, distributed points of presence etc.) and if the end-user has a larger system they need to stay with these manufacturers.
When looking at the deployment of the system, the end-user must decide whether they want the TATA or the BMW. If it is a simple one- or two-door deployment, the TATA may be just the device (for a simple application), but it won’t be able to handle 30 or 40 doors on one system – it will fall over.
This is where the BMW comes in. It was designed for SMME and enterprise systems, with all the bells and whistles required (i.e. access control, T&A, meal management, integration with PSIM systems, integration with logical access control, compliance with fire bylaws, ability to easily integrate with third-party management software solutions etc.). Currently ViRDI has the largest commercial biometric deployment in the world with more than 300 000 enrolled users, more than 4000 terminals and more than 1 000 000 transactions per day on a single system. The TATA will never be able to handle this type of deployment.
Biometric technology advice
Stay away from anything that looks and smells cheap because invariably they are and the end-user is going to spend money on this technology only for it to fail and quite possibly result in them renouncing biometric technology as a failure. Ensure the product is available from multiple sources, that technical support is available all through the value chain, that repairs can be done in country and most importantly, if the company that supplied the device originally is unable to provide further support, service and maintenance, that another supplier can step in easily to assist them.
Look for devices that have IP ratings – Africa is harsh on electronic devices and you don’t want a device that will fail at the drop of a hat because of our environment. Lastly, look for a biometric system that can easily integrate with other software packages, such as T&A or software management suites.
For more information contact ViRDI Distribution, +27 11 454 6006, [email protected], www.virditech.co.za

Suprema Africa, Walter Rautenbach
Suprema is another South Korean biometric company that is present in around 133 countries around the world. It was the first biometrics company listed on Korea’s stock market and is represented in Africa by Suprema Africa, a distribution division of neaMetrics. neaMetrics CEO, Walter Rautenbach answers our questions on fingerprint biometrics.
The purpose of a fingerprint scanner is to capture a fingerprint image. Basically, it is a replacement for the old way of putting ink on your finger and then placing it on a piece of paper. The closer it gets to what it actually looks like on paper is a big part of how good the fingerprint sensor is and that is where international certifications of image quality such as NIST (National Institute for Science & Technology) Image Quality Standards, abbreviated as IQS, as well as specific FBI standards come into play.
These standards normally confirm that the image the fingerprint scanner returns is classified as a true representation of the actual finger. One might ask why are we comparing it to paper impressions, is that not outdated? The simple answer is that a very large portion of fingerprint data stored on current Automated Fingerprint Identification Systems (AFIS) originates from paper records. Although living in the age of digitisation, records originating from paper records will still be here for many years due to historical records, lack and cost of digital infrastructure, and because paper records are still actively used in the process of crime scene data collection.
A functional fingerprint system always includes two elements, enrolment and matching. Enrolment is the process where the fingerprint is captured, fingerprint template extraction is performed (although this can be done at a later time) and where either or both the fingerprint image and template is stored on a database.
The second function, and really the main purpose of a biometric identity system, is the process of matching a fingerprint against a previously recorded enrolment. Although loosely referred to as biometric identification, the matching can really be classified as either authentication or identification. Authentication, also known as verification, is where biometrics of a known person are captured, template extraction is performed and then matched against the person it claims to be from on the database. Typical samples of authentication are when you supply your ID, card, user name or some personal data to enable retrieval of your record, and where you need to confirm you are who you say you are (i.e. applying for a passport, authorising a financial transaction or in some cases where you log into your PC or mobile device).
The process of identification is then different from authentication because during identification, a specific identity is not claimed and confirmed, but rather a biometric template is extracted and used to find a person on a database with many enrolments to establish who the person is. When the police find your fingerprints at a crime scene, they do not know who you are and the latent fingerprints found at the scene are scanned against the database to see if it can find a person on the system due to previous crimes. Identification is also used as a form of convenience, for example with access control, to avoid the inconvenience of presenting a card or entering an ID – just place your finger to see if you exist and have access.
The main differentiator between fingerprint identity systems is whether the fingerprint image or only the extracted fingerprint template is stored. General consumer-based systems, such as access control and T&A, only store the fingerprint templates. The main motivators for only storing templates is that it is more secure (if someone steals your fingerprint image it is almost as good as chopping off your finger).
Templates are also much smaller in size making it faster to transmit them, as well as easier to store a lot of people on a small device. Unfortunately, some systems need to store the image and the reason for that is so that it can be visually confirmed by a fingerprint expert in a court of law, or on a large AFIS system that can possibly return multiple matches or HIT candidates. It is with these systems where the importance of the fingerprint image truly representing the actual finger, and the associated certifications relating to this, plays a vital role.

Looking at standards
Institutions such as NIST and the FBI are forerunners of standards and benchmarking systems. This can broadly be subdivided into two categories: the fingerprint image produced by the fingerprint scanner on the one hand, and fingerprint algorithms on the other.
When looking at fingerprint images, the FBI certifications Appendix F/G, PIV, FAP and more exist, basically prescribing the quality and size a fingerprint scanner should produce. Quality, in layman’s terms, refers to how well it represents the actual fingerprint, and size, which does matter because the more of the fingerprint that can be captured, the more data that can be used by the algorithms that process the images.
Fingerprint algorithms, or at least the good ones, normally offer two types of extraction, one that produces proprietary templates, of which the content and structure is unknown and only usable by the manufacturer’s system, and then the second being the production of an open standard, normally ISO/ANSI compliant fingerprint templates. Where ISO/ANSI templates are produced, they can be used by any vendor supporting these standardised templates, and since the structure is open, the core finger data being extracted can be evaluated by a fingerprint expert by plotting bifurcations and ridge endings on the image to verify the accuracy.
It is for this reason that NIST, in collaboration with the fingerprint community, started MINEX, short for Minutia Interoperability Exchange. There are various MINEX standards all focusing on cross vendor interoperability. Here vendors get the opportunity to do fingerprint template extraction (extracting minutia) from a given data set and then to benchmark their matching algorithm, or other open standard algorithms, using open standard fingerprint templates against a large and given fingerprint test data set. Vendors that participate in these tests get a performance ranking across other vendors, but remember that rankings change on a daily basis as vendors rework their algorithms to deliver better results. I consider the impact of MINEX as exceptional, not only because it focuses on interoperability, but also because it drives vendors to continuously improve.
Looking specifically at the matching capabilities of proprietary fingerprint algorithms, not using open standards, then FVC (Fingerprint Verification Competition) is a well-known benchmark. It started as a competition every second year, but the last was in 2006 after which they progressed to FVC-onGoing, allowing participants to do the test again at any time. This means a vendor can tweak, test, tweak – instead of waiting for two years, which once again is great for algorithm improvement.
Buyers must ensure their selected vendor does not boast about their algorithm improvements based on internal results, but use internationally recognised test benches and standards such as MINEX, FVC-onGoing and others recommended or prescribed by institutions such as NIST, FBI and ISO biometric workgroups.
Security and privacy
Fingerprint images are more hackable than fingerprint templates, but in both cases, with today’s technology, rebuilding a modelled 3D image of a finger is not impossible and most likely is already being done. Even if an un-hackable fingerprint image or template was available, and I really wanted your fingerprint image, why would I not just find a way to lift your latent print off an object you touched and then use the same to recreate that modelled fingerprint?
Deterrence of unethical access and use of biometric identity data can only be achieved through continuous change and a vendor and/or solution provider that follows the same principles and who is willing to openly and honestly consult. To not obfuscate or avoid answering the question with some usefulness, the following are some of the deterrents at hand:
Liveness detection: Perhaps the simplest solution is using fingerprint hardware as well as algorithms that detect fake fingers. We have to continue monitoring what defines ‘live’, especially with 3D technology venturing into organ production.
Data protection: All solutions should ensure to encrypt both data being communicated and stored using internationally recognised and current encryption standards. It is not uncommon for solution providers to apply proprietary obfuscation over and above recognised encryption since continuous efforts are being applied on a daily basis by ethical and unethical parties to break recognised encryption standards through mathematical and brute force mechanisms. Although this does complicate things for hackers, it also creates a ‘proprietary’ threat to the vendor who might be vulnerable to lock down. The benefits and downfalls of each need to be evaluated on a case-by-case basis.
Biographic and biometric data separation and fragmentation: Separating biometric and biographic information across infrastructure helps protect data. For example, should a hacker gain access to a server with biometric data, where no personal data or identifiers exist, the usefulness of the data deteriorates. In other words, if I get access to all biometric data for Bank X, but I do not know whom they belong to, how would I use this data to do fraudulent authentication? As a hacker, I would now have to hack into another infrastructure stack and identify how these two data sets are linked.
Suprema’s technology
Suprema’s range of enrolment and authentication finger sensors, and selected access and T&A range complies with various FBI regulations. These include PIV, Mobile ID, FAP and Appendix F, designed to ensure compliance to image quality and size regulations. It is important to note that the nature of the certifications do not allow all fingerprint readers to have all certifications. For example, due to its size, a slap or palm scanner does not fall into the Mobile ID certification range and Appendix F is designed for FAP45 (FAP relates to specific sizes) and up.
Most of Suprema’s fingerprint scanners also include liveness detection, some in the form of hardware components and some using software based or machine learning techniques to detect fabricated fingerprints. This technology is referred to as Suprema’s Liveness Detection Engine (LDE) and more information can be found at https://www.youtube.com/watch?v=1MTkGWXgfQg, or at http://kb.supremainc.com/knowledge/doku.php?id=en:tc_whitepaper_suprema_live_finger_detection
A big challenge in the past was the capturing of dry and deteriorated fingerprint images, so some vendors introduced multispectral imaging technology that overcame these challenges and gained huge popularity, including the South African market due to a large part of the identity population’s involvement in hard labour, as well as old age (pensioners).
Multispectral technology performance is exceptional, but not 100% understood. Multispectral imaging technology produces an image that can even detect subdermal traits, meaning worn fingerprints can function normally. The downfall of this technology is that it does not produce an image that looks 100% like the original and for this reason, FBI certification is not possible.
In instances where these images are being used for authentication, against systems where AFIS data population is done by means of paper scans and FBI certified optical technology, the results will not be as accurate as when using good certified optical hardware. One must keep in mind that a multispectral image in its original form does not look like a normal fingerprint image. Image processing is performed to produce a compliant 500 dpi greyscale image and since subdermal elements are not present in standard optical or paper records, these can influence match results.
Suprema developed its own patented technology referred to as Multi-dynamic Range (MDR) technology, now implemented on all its new fingerprint authentication and access and T&A terminals with exceptional results. The technology can be compared to the changes from High Definition (HD) television to Ultra High Definition (UHD) or even 4K when comparing the results. More can be read here about this technology at http://kb.supremainc.com/knowledge/doku.php?id=en:tc_technology_multi_dynamic_range_technology
Suprema’s fingerprint algorithms are ISO/ANSI compliant and involvement in and with top results at FVC-onGoing and MINEX illustrates involvement in industry benchmarking as well as the quality of the results it delivers. The top MINEX results further show that Suprema algorithms do not only perform well in its proprietary systems, but also where open standards are used in biometric identity.
Advice to buyers
Different use cases can be based on needs and purpose. In all cases, we expect biometric technology to positively confirm or identify a person, with tolerances only accepted based on the limitation of the science of fingerprint mathematics. In summary to the previously provided data:
• Determine if your system requires you to store fingerprint images or only the templates. If images are required, then do ensure your fingerprint scanner complies with known certifications (i.e. FBI and NIST quality standards).
• Enrolment vs authentication. Keep in mind that initial enrolment, or reference data collection, is the most important part of a biometric identity solution. A bad enrolment will result in poor matching performance.
• Difficult fingers. Not all fingerprint hardware is the same. Make sure to test your considered vendor hardware on people that have experienced problems with their fingers in the past
• Liveness detection. Does your vendor provide liveness detection options?
• Does your vendor have a large-scale international track record?
• Have the algorithms, that you use, been benchmarked? Various international benchmarking platforms/bodies exist (NIST/FBI/FVC/MINEX). Investigate this before you purchase.
• Is your vendor compliant with open standards?
• How will the data on your system be protected? Is data encrypted and are internationally accepted encryption standards used? Does your vendor adhere to data protection regulations such as PoPIA and GDPR?
The above are some questions that need to be asked before initiating a fingerprint identity system. There are many more considerations to be evaluated on a case-by-case basis. The most important question is if you have a reliable partner, with extensive experience in the field, that can offer you good advice from the beginning, guide you through the lifetime of your biometric identity system and who keeps abreast with daily technology developments to ensure your system remains an asset and does not turn into a liability.
For more information contact:
• neaMetrics, +27 11 784 3952, [email protected], www.neametrics.com
• Suprema, +27 11 784 3952, [email protected], www.suprema.co.za

HID Global Lumidigm: Claude Langley
Part of ASSA ABLOY, HID Global focuses on trusted identities that make it possible for people to transact, work and travel. The company absorbed Lumidigm a few years go and the company now functions as a biometric division of HID. Claude Langley is the biometrics business development manager for Africa at HID Global – Lumidigm.
The three most common technologies used for fingerprint sensors are multispectral (HID), optical and capacitive. Each technology varies in its ability to capture an image, determine its liveness and match against the stored information.
Fingerprint sensors essentially all take an image of a fingerprint, which is captured when an individual places their finger on the sensor platen, yet not all technologies provide equivalent results. Once the image has been captured, either the sensor or the back-end biometric system extracts specific unique characteristics of a fingerprint from the image, called minutia, to create a unique template.
Depending on the architecture of the biometric system, a fingerprint sensor can do either of the processes below:
• Take an image and send it to the database to conduct the minutia extraction and one-to-one (1:1) or one-to-few (1:N) match on the server.
• Take an image and conduct the minutia extraction and template generation on the sensor, sending only a binary data string (template) to the database to perform a 1:1 or 1:N match on the server.
• Take an image and conduct the minutia extraction and template generation on the sensor, then request the template linked to that individual from the server or a smart card to conduct a 1:1 match on the sensor.
• Take an image and conduct the minutia extraction and template generation on the sensor, then perform a 1:1 or 1:N match to template(s) stored on the device.
There are various international standards to regulate how fingerprints are scanned, processed and stored. Common image format standards are WSQ, ISO/IEC 19794-4:2005 and ANSI/INCITS 381-2004. Common template interoperability standards are ANSI 378 and MINEX III all of which are supported by multispectral sensors.
‘No Match’ or ‘False Reject’ errors can happen for a variety of reasons, most of which are not related to the image format, but rather to the quality of the information received. If an image is used, then it’s necessary to capture and distinguish real fingerprint minutia from dirt particles, water, dry skin, etc. If poor information is captured, only from the surface of the skin, then this information will also not suffice to provide the expected match.
The privacy question
The use of templates does create a layer of obfuscation that will make it more difficult for a ‘hacker’ to reverse engineer a fingerprint minutia template to a full fingerprint. However, the danger does exist. This reinforces the point that fingerprint sensors should include a highly sophisticated liveness model to ensure that the data being matched is not only correct, but it is confirmed to be generated from a living person. If liveness is utilised in conjunction with the fingerprint information, the fear of identity theft can be reduced, if not removed altogether.
Secondly, fingerprints are not private. While they are unique, we leave them everywhere we go, on glasses at restaurants, tables, door handles, walls, elevator buttons, etc. To obtain someone’s surface fingerprint data, one does not need to hack a database and reverse-engineer a fingerprint template. They just need to pull a fingerprint like is done at a crime scene. The combination of liveness plus high performance is what creates the true value of fingerprint biometric sensors.
HID’s fingerprint technology
HID biometrics uses a patented technology called multispectral imaging which was specifically developed to overcome the fingerprint-capture problems that have plagued conventional fingerprint sensors when they are used in the real world – outside the lab.
Multispectral imaging utilises multiple spectrums of light and advanced polarisation techniques to extract unique fingerprint characteristics from both the surface and subsurface of the skin and to determine relevant fingerprint data. Subsurface capability is important because the fingerprint ridges seen on the surface of the finger have their foundation beneath the surface of the skin in the capillary beds and other sub-dermal structures.
Unlike surface fingerprint characteristics, which can be obscured during imaging by moisture, dirt or wear, the ‘inner fingerprint’ lies undisturbed and unaltered beneath the surface. When surface fingerprint information is combined with subsurface fingerprint information and reassembled in an intelligent and integrated manner, the results are more consistent, more inclusive and more tamper resistant. The use of multispectral imaging also contributes to our industry-leading liveness detection.
As of the printing of this article, HID V series multispectral imaging sensor is the only sensor to achieve a perfect 100% detection of fake finger attacks during the ISO/IEC 30107-3 Presentation Attack Detection (PAD) standard certification testing process. (See more at https://www.hidglobal.com/press-releases/hid-global-lumidigmr-multispectral-fingerprint-technology-earns-first-perfect-score.)
Many of HID Global’s Lumidigm sensors also offer the use of the Innovatrics MINEX III algorithm. As published by NIST on the 12th of November 2015, HID became the first vendor to achieve full PIV compliance in MINEX III while also ranking first in most of the main accuracy and interoperability criteria. The Innovatrics template generator is one of the most accurate out of all vendors and the Innovatrics template matcher performed the best in the native one-finger ranking where it was placed first among all submissions.
The bottom line is that HID’s multispectral sensors offer the best performing sensor for image quality combined with the best liveness detection available. If matching is required on the sensor, we offer a top-ranked minutia extraction and matching algorithm.
Recommended technology for Africa
The fingerprint sensor should match the use case, yet in most cases where fingerprint biometrics is used, the goal is to properly validate the identity of an individual. Typically, performance matters and adoption of the technology is hindered if authorised individuals are not matched quickly. Liveness should matter as the true value of biometrics is only realised when it is used.
The potential impact of poor accuracy to a government or a banking application can be significant compared to a factory time and attendance application. Organisations need to understand the level of attack sophistication, frequency of attack and the value of what they are protecting. There are over 35 000 different materials which can be used to make fake fingers and hundreds of videos on the Internet on how to make them.
Government entities, banks and factories must all consider the diversity of finger types in their user population and base their requirements for biometric technology on these factors. HID’s multispectral imaging technology captures details below the surface of the finger and therefore performs capture, liveness detection and matching on all the most difficult finger types.
Purchase considerations
There are many considerations when making a buying decision on biometric technology. The three most important include:
• Capture: How effectively does the sensor match my authorised individuals on a consistent basis over time in the real-world setting? This is covered by the metrics related to the ability to capture usable biometric data on the first attempt for every user. Ability to capture is the most essential performance consideration in commercial biometric applications. Consumers expect ‘100/100’ capture performance, even in challenging environmental conditions and for diverse populations.
• Liveness: How effectively does the fingerprint sensor determine whether the fingerprint is real or is a fake? Liveness detection refers to the ability to confirm that the captured finger image is legitimate and from a live finger by comparing complex optical characteristics of the material presented against known characteristics of living skin. This unique ability of multispectral imaging provides accurate fingerprint liveness detection and eliminates the perception that fingerprint images must be kept secret to be trusted for user authentication. Fingerprint images are not secrets.
• Match: How effectively does the minutia extraction and matching occur? Is the data interoperable or am I locked into a proprietary template format that requires me to purchase only a certain type of sensor? To prevent vendor lock-in and to provide choice for users of commercial biometric systems, fingerprint authentication solutions should use interoperable and independently tested global fingerprint minutia standards. HID Global’s fingerprint matching technology uses existing ISO 19794-2 templates supplied by a tier-1 MINEX III certified algorithm for fingerprint templates, including ANSI 378 and ISO 19794-2 MINEX templates supplied by a Tier-1 fingerprint algorithm partner, independently tested and validated by the U.S. National Institute of Standards and Technology (NIST).
For more information contact Claude Langley, HID Biometrics, +27 83 321 2922, [email protected]

IDEMIA: Gary Jones
The combination of Oberthur Technologies (OT) and Safran I&S (Morpho) resulted in IDEMIA, a company that has coined the term Augmented Identity. Gary Jones is the VP for channels and marketing at IDEMIA (see more in the article ‘Taking augmented identity to the world’).
The first stage of fingerprinting is referred to as ‘acquisition’ because the sensor acquires an image of the fingerprint, which is a pattern of ridges and valleys.
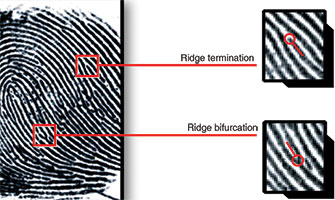
Next comes the feature extraction phase during which the unique features of the print (referred to as minutia, are detected and extracted). Minutiae are the points where ridges start or end (terminations), or where they split from one into two (bifurcations), as well as various combinations thereof.
The image below shows the process including an advanced method of enrolment using multiple acquisitions of the same finger which are compared/matched against each other, and then consolidated to create a more complete and reliable template.
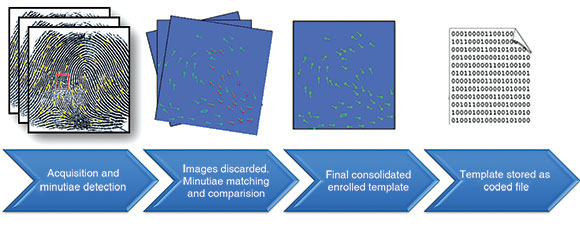
International biometric standards
Biometric sensor standards govern both the image size and quality produced by a sensor. They define parameters such as resolution (ppi), distortion, illumination consistency as well as image dimensions. FBI PIV IQS is the standard most commonly relied upon for sensors used in access control and/or time and attendance.
There are also standards for biometric template generation, such as the ANSI INCITS 378 format, which is designed as a common template format which can be used by any vendor. This resultant interoperability allows templates generated by a system from manufacturer A, to be compatible with a system from manufacturer B, and so on.
Most major biometric vendors submit their algorithms to NIST (National Institute of Standards & Technology) for independent benchmarking. These benchmarks are heavily relied upon by major users of biometrics, but equally present a valuable resource for smaller customers to determine the robustness and performance of a given vendor’s biometric algorithms, now and over an extended period as the benchmarks have been running for multiple years.
This can help determine how long a vendor has demonstrated leading performance, how consistent their solutions are over time, and how much they invest in R&D to ensure continuous improvement of their products over time.
NIST conducts benchmarks for both proprietary and interoperable template formats, and it is important to select a vendor with strong performance in both domains to ensure robustness and future proofing of the enrolment data and solution.
Preventing identity theft
This also ties back to the encoding process mentioned above. Additionally, there are four key aspects needed to prevent against identity theft risks:
The nature of data stored.
• One key reason biometric systems discard the image is to make the process of reverse engineering as complex or improbable as possible. Even if we assume a hacker somehow gets hold of a template, a reverse engineering process will always result in differences from the original image (as it will be a synthetic/generated image from a much smaller subset of data).
• This is analogous to a children’s join-the-dots drawing. You can join the dots in the correct order millions of times, but depending on how the lines flow, every resultant picture can look slightly different, and even small differences can have a significantly negative impact when matching fingerprints.
• Irrespective, the process of reverse engineering is a very complex one and typically not worthwhile for reasons described below.
System security architecture
At a high level, this includes:
• Hardware/software architecture and resultant robustness against physical and network penetration,
• Defining access roles and privileges, and
• How the data is encrypted at rest and during transmission.
Spoof detection
This is a key line of defence in biometric systems. Today’s leading technologies employ complex mechanisms to determine if the biometric being presented is genuine or some kind of 2D or 3D spoof attack (such as a fake finger or hand). This drastically reduces the risk or threat posed by stolen or hacked biometrics
Multi-modal or multi-factor authentication
• By incorporating two biometric factors (e.g. face and fingerprint), the security of a system can be increased even further. Similarly, by scanning more than one finger on a hand the accuracy is increased whilst also increasing the complexity of spoof attacks.
• Incorporating a card and/or PIN in addition to the biometric (or any combination thereof) can also be used to further strengthen the robustness of a system against attack
o Something you know
o Something you have
o Something you are
No system is 100% bulletproof, but one can design a system to make the level of effort far outweigh either the reward, or alternate means of achieving the same goal.

Technology from IDEMIA
As the global leader in biometrics for over four decades, IDEMIA manufactures a wide range of FBI PIV IQS-certified optical sensor technology for access control and time and attendance markets. These include:
• High-speed touchless 3D fingerprint sensors (MorphoWave) which scan all four fingers with a simple wave of the hand.
• Large area contact-based single fingerprint sensors used in our MorphoSmart and MorphoAccess Sigma readers.
In addition, IDEMIA’s fingerprint algorithms are consistently ranked #1 on NIST benchmarks and are trusted by the world’s largest users of biometrics. Due to the strength of our algorithms we are able to offer customers the ability to configure a security threshold (assurance level) that is strictly enforced by our readers irrespective of the database size. Cheaper biometric products typically suffer from performance/accuracy degradation as the user population grows.
Unlike many cheaper alternatives, our technology is designed and built to last, and therefore ensures the highest ROI. This is validated by the large number of customers who are still using Morpho readers installed almost 20 years ago, which are still performing better than many new entrants on the market today. Our sensors and algorithms are proven in the harshest industries and environments, and comply with major industry standards.
Our most advance offerings, MorphoWave Compact and MorphoWave Tower, are in a league of their own. The 3D imaging technology is able to acquire up to 30% more data from each finger and scan all four fingers multiple times in 3D during a single wave. This is faster than many competing readers can scan one finger in 2D.
With in-motion matching, users do not need to stop or pause at the reader, resulting in throughput exceeding 45 people per minute. A major breakthrough with this technology is that both security and convenience are increased simultaneously, therefore requiring no compromises.
User and technology recommendations
We regularly see some important fundamentals being overlooked in the commercial sector. Clients often choose to buy cheaper technology because they don’t think of themselves as having the same accuracy requirements as a major government organisation, for example. However, a few simple examples can be used to illustrate the importance of accuracy and its impact on cost:
• In a time and attendance system, every false clocking (either because a fingerprint did not match, or worse, matched incorrectly) leads to downstream payroll errors that require human intervention to correct. This has a direct labour, time and financial cost, which over only a few months can exceed the cost differential between a cheap biometric system and an industry-leading biometric solution.
• In an access control application, a company with 1000 employees transiting through a conservative five access points per day, may have over 1 million access transactions per year. We often see cheaper biometric systems being configured with low matching thresholds such as 1 in 1000 False Accept Rate (FAR) in order to avoid high levels of inconvenience due to False Rejection Rate (FRR). This would result in approximately 1000 incorrect false authorisations per year, leading to a high risk or fraudulent access and making the system audit highly questionable.
In addition to potential theft or malicious attack related losses, implementing an insecure system opens the organisation to significant liability risk.
South African organisations should look closely at the total cost of ownership when selecting a biometric system. Referencing major benchmarks such as NIST and researching which technologies are trusted by major organisations such as Interpol and the FBI, who rely heavily on biometrics, is a reliable indicator of which technology is thoroughly proven, can scale well, and ultimately can be trusted.
Factors such as local support from the manufacturer in conjunction with a well-established channel network of resellers and installers in the region should also be considered. Another factor is how long the vendor/manufacturer has been present in the market. A biometric system should be looked at as an investment that should last a minimum of five years but typically 10+ years is common for industry leaders.
In other words, never compromise. A more accurate, proven solution will pay for itself within months when compared to cheaper alternatives.
For more information contact IDEMIA, +27 11 286 5800, [email protected], www.idemia.com
| Tel: | +27 11 543 5800 |
| Email: | [email protected] |
| www: | www.technews.co.za |
| Articles: | More information and articles about Technews Publishing |
© Technews Publishing (Pty) Ltd. | All Rights Reserved.