
Employee verification covers a lot of ground as it confirms people’s identities, qualifications and more, but as we head into a more connected world, is it enough to simply make sure the person you are hiring (or running a regular check on) is who they say they are? In a world where it is harder than ever to dismiss employees, and where reputations are destroyed almost instantly, and where someone’s ability to fit into an organisation and team is potentially more important than their qualifications, perhaps it’s time to look deeper.

iFacts has been in the employee verification game for many years offering employee verification screening to various industries, including the security market. While there are extensions to traditional verification, such as integrity tests (discussed in another article in this issue), Hi-Tech Security Solutions spoke to iFacts CEO Jenny Reid about how the company has expanded its services to look beyond traditional verification.
Reid says iFacts has expanded its scope of operations to include new profiling areas in its overall services. While these don’t focus in verifying the identity and qualifications of people, they add to the traditional verifications services iFacts offers. Summing up the focus of these additional services, Reid explains they consider the ‘risk of employee engagement’, or give companies an idea of what risks they may face in future with these people on board.
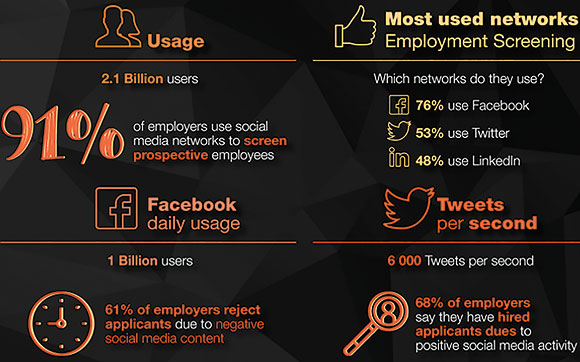
There are a few trends in this risk aversion strategy, and one focuses on social media. With billions of social media accounts around the world, and hundreds of millions active in South Africa – including Facebook, Twitter, Google Plus, LinkedIn and many more – the implications of what people do on social media are vast. We only need to look at Chris Hart or Penny Sparrow (and the list goes on) to understand what one careless post can do to a person as well as the company they work for.
Social media screening
Social media screening goes beyond simply looking at someone’s Facebook or Twitter page. This service, which iFacts offers in partnership with Farosian, measures the potential risk an individual could pose to a company.

An example of this risk Reid offers is that of an individual who seemed an ideal candidate for a position of responsibility. An overview of her social media account backed this view up, until a more in-depth study was made. It was then found that she had posted highly controversial comments in the past that were homophobic, among other things. If the company had hired her, it could have faced significant reputational and potentially financial damage at a future date.
The problem, Reid says, is that people are more open on social media that they would be in real life, and often inadvertently (or purposefully) publish things they would not want out in the open. The screening service iFacts offers looks beyond a few posts and delves below the surface most people see. To be fair, it also considers multiple factors when running the profile search, such as age and the situation in which posts where made to ensure the risk assessment is fair and relevant to the person’s potential position.
Reid also notes that iFacts always obtains the individual’s permission to do the social media screening in advance to avoid any legal grey areas.
More than a scan

It’s safe to say that social media screening is not new. Many companies have in-house staff to do these types of jobs, but Farhad Bhyat, CEO of Farosian says they are often based on inadequate information or done by simply browsing someone’s feed. “There are no qualitative or quantitative rules involved to ensure the job is done professionally and in the required depth.”
He provides an example of a company in the USA where an individual was given a letter of appointment, but then told she would not be getting the job when she arrived for her first day of work. It turns out that after the position was offered to her, someone in HR did a social media scan and found a mugshot of someone with the same name. That was enough for the company to withdraw the offer. Unfortunately, while the names were the same, it was not this particular individual in the mugshot. She then sued the company and won a large amount of money.
Farosian looks beyond simple page scanning or Google searches (and makes sure it has the right person). The company uses automated processes for the majority of its screening, which covers multiple social media sites, but Bhyat says there are always some manual processes involved to ensure the profile is accurate and reflects the actual level of risk the individual may pose to the company.
This result of the profile will not give away any personal details of the individual, but will simply offer the level of risk they pose for the company based on their score. The risk levels range from ‘Very Low Risk’ up to ‘Extreme Risk’, while the scores are awarded in various criteria, including the individual’s creativity, communications skills, professional image, teamwork and collaboration, critical thinking and more.
Another differentiator in Farosian’s screening is that it looks at both the positive and negative issues of the individual. Context is also important in this respect. If someone has a few drinks at his birthday party that is acceptable, but if he has a few for breakfast that could indicate a problem. Other issues the company looks for could include if the person can engage in arguments constructively. This may indicate if they are likely to cause conflict in the workplace and if they would be a good team player.
For those who think social media screening is a little dramatic and that a social media scandal would simply be a bit of a controversy without any real impact on the company, Bhyat explains that this simply is not true. Even though the individual may not have been posting on behalf of the company, they are still associated with the company and the online reaction will impact the company.
In one incident, he notes that the individual’s employer, a national real estate agency, did not make a sale for six weeks after the scandal began despite having 600 agents on its payroll. People just avoided the company because of the scandal. Bhyat states that the cost of South African social media scandals in 2016 is around R450 million.
More recently, United Airlines in the USA became the latest company hit by a social media scandal after a doctor was dragged off a flight. Within a few hours of the incident, around $900 million had been wiped off its valuation. Much of this loss was recovered, but at the time of writing, it was still $250 million down on its pre-incident value. Moreover, three of its competitors saw an upturn in their stock prices during the same period.
Farosian does not tell employers to hire a person or not. It simply fills a gap in the traditional screening processes by highlighting potential risks associated with the person. The company also provides training to assist companies in developing social media policies which are comprehensive and able to deal with any surprises their employees or anyone on social media may throw at them.
“We all need to realise there are no secrets,” Bhyat concludes. “Even if you try to restrict access to your social media posts, there are always ways to see what you’re doing, even for people who are not friends or followers. And there is no delete key; once it’s published it’s available for those who know where to look.”
It’s not all bad news, however. Reid explains that people with a low-risk social media profile will find it adds value to their CVs, increases the chance of a successful job interview, and can even enhance job security.”
Oh behave!
Another trend in verification and screening focuses on behaviour. Reid notes that we are all different and are motivated differently. Simply look at millennials and you will understand that motivation and behavioural characteristics differ.
When hiring someone, a company wants to know that the person they are going to invest time and money into is a good fit for the company and its culture, and is able to do the job. This is where a PDA (Personal Development Analysis) comes into the picture. The PDA is a tool that through a simple, yet accurate and scientific methodology, allows you to describe and analyse the behavioural profile of individuals.

iFacts partners with PDA Africa to conduct personal development analysis on individuals to determine their behaviour profiles. Wade Cooper, CEO of PDA Africa explains that PDA assessments allow companies to hire the right person for the job, make sure the best talent works together in teams, develop leadership skills and assist in succession planning, and identify areas where employees or potential employees need to be trained to deliver the optimal performance.
PDA Africa is part of PDA International, which offers its services globally. The local company offers its services in 18 African countries out of the 47 countries served internationally. It has hundreds of partners globally that take its assessments to market, with iFacts operating as a partner in Africa.
Cooper says that the assessment conducted by PDA is scientifically based with a 90% reliability coefficient. This means employers can rely on its findings to determine people’s behavioural characteristics. The report, which can be produced in various languages (the assessment is also available in multiple languages) can assess areas such as leadership or business style, strengths and limitations, motivation, compatibility with key competencies of the job being applied for and assists in improving productivity.
The assessment is not a test with right or wrong answers, it simply measures each individual’s behavioural characteristics. Cooper says the benefit of PDA Africa’s approach to assessments makes it the easiest way to create a behavioural profile of an individual.
The assessment is called the PDA Human Capital Management System and is completely online. It takes an individual 10 to 15 minutes to complete. In cases where individuals may not have access to the Internet, the assessment can be completed with pen and paper. PDA Africa does not charge a licence fee to access its site, but limits the costs by charging per report. Cooper notes that each ‘PDA credit’ allows a person to conduct one assessment and receive a full report – the company does not charge for different aspects of the report.
To administer the assessment and understand the report, companies like iFacts need to send the relevant staff on a three-day course to attain a certification.
Customised reports
Cooper adds that the assessments are not vanilla assessments that are provided for every potential employee. It is a scientific way to look at behaviours in comparison to the job description the individual is applying for as well as the competencies required. The report provided to the company will compare the individual’s personal behaviour profile to the job and competency profile provided, allowing the employer to make informed decisions as to the person’s fit to the job and the company.
He also notes that traditional verification and screening processes are still required, but should be combined with PDA profiling to ensure the right person is employed in the right job and the right environment.
“All too often we hear that people are hired for their technical skills, but fired for their faulty behaviour,” he notes. “The PDA assessment overcomes the behavioural ‘unknowns’ and allows companies to hire people they know will fit into their culture and are capable of performing the job.”
He adds that many educational institutions are also using the PDA assessment as a means to make their graduate development programmes more effective. These organisations can now scientifically identify issues graduates may have in the workplace and deal with them before the students get a rude awakening or hiring companies wonder why they hired them.
The PDA is also a good method for individuals to assess themselves in terms of how their particular behavioural patterns will fit in as well as provide insights into any personal development they may require.
When this reporter completed the assessment, provided by PDA Africa, the process took only 10 minutes and the report provided concise insights into the personal and role-based behaviours pertinent to my job. It would offer managers and HR administrators keen insights into the type of environment suited to the individual, as well as the ways to manage and motivate the person most effectively.
PDA Africa is also committed to social development in Africa. Cooper says 80% of the company’s partners in Africa are women owned and the company was awarded the first runner-up position in the category of Women Empowerment in the Workplace at the 2015 Gender Mainstreaming Awards ( http://www.genderawards.co.za/the-awards/the-winners-2015).
While the verification of people’s identities and other information is still a critical aspect of the hiring process, the world we live in today has made it a risk to hire people without additional information to assist in deciding if they will be a good fit for the company and are likely or unlikely to cause the company any brand or reputational harm in the long run. If one takes the New York Times seriously, its recent article ‘The Utter Uselessness of Job Interviews’ (www.securitysa.com/*nyt1) highlights the need for additional mechanisms to assist in deciding who fits in a job and who doesn’t. Social media screening and behavioural assessments are two candidates with a good background in providing useful and usable information to companies and individuals.

For more information contact iFacts, +27 (0)11 453 1587, jenny@ifacts.co.za, www.ifacts.co.za
| Tel: | +27 11 453 1587 |
| Fax: | 086 523 0648 |
| Email: | info@ifacts.co.za |
| www: | www.ifacts.co.za |
| Articles: | More information and articles about iFacts |
© Technews Publishing (Pty) Ltd. | All Rights Reserved.